Microsoft Defender for Endpoint Testground
Do you often find forums discussing Microsoft Defender for Endpoint and its features, but still have questions in mind?
🚀A one-stop solution for all your questions- We have started a Microsoft Defender for Endpoint Series, where we want to cover topics on a deeper level and discover the possibilities with all kinds of threats and endpoints!
Fig i) Learn Microsoft Defender for Endpoint with #Salona aka #Intunesiastic
In the previous blog, we gained detailed knowledge on the key capabilities of Microsoft’s Threat and Vulnerability Management in Microsoft Defender for Endpoint. By far we have covered the basics for the Windows Platform and have also set up the Microsoft Defender for Endpoint as shared in the snapshots from my test environment. Furthermore, today I would like to share with you a perfect Test-kit to try out how good the Microsoft’s Defender mechanism works!
Microsoft encourages you to test Defender for Endpoint and it’s capabilities using it’s sample files. These files do not contain any harmful or dangerous data but these would only poe as malicious.Your environment which is being secured by Microsoft Defender for Endpoint will identify the file to be malicous just to give you the feel of how it shall protect the machine in a real-time scenario.
It is recommended to read the Microsoft Defender Antivirus documentation, and download the Evaluation guide. None of the sample files are actually malicious, they are all harmless demonstration files.
The demonstration scenarios are provided for the following Microsoft Defender for Endpoint protection areas:
- Attack surface protection (ASR)
- Next Generation Protection (NGP)
- Endpoint detection and response (EDR)
1) Attack Surface Reduction (ASR)
Reduce your attack surfaces by minimizing the places where your organization is vulnerable to cyberthreats and attacks. For more information please refer to the attack surface reduction documentation, and download the Evaluation guides.
- Network protection demonstrations– Navigate to a suspicious URL to trigger network protection.
- Attack surface reduction rules (ASR rules) demonstrations– Download sample files to trigger each ASR rule.
- Exploit protection (EP) demonstrations– Apply custom exploit protection settings.
- Controlled folder access (CFA) demonstration (block script)– Download the CFA test tool.
- Controlled folder access (CFA) demonstrations (block ransomware)– Download and execute a sample file to trigger CFA ransomware protection.
2) Next Generation Protection (NGP)
- Validate antimalware – Confirm that antivirus/antimalware is detecting and blocking malware.
- Potentially unwanted applications (PUA) demonstration – Confirm that potentially unwanted applications (PUAs) are being blocked on your network by downloading a fake (safe) PUA file.
- Cloud-delivered protection demonstration – Confirm that cloud-delivered protection is working properly on your computer.
- App reputation demonstration – Navigate to the app reputation page to see the demonstration scenario using Microsoft Edge.
- URL reputation demonstrations – Navigate to the URL Reputation page to see the demonstration scenarios using Microsoft Edge.
3) Endpoint detection and response (EDR)
- Endpoint Detection and Response (EDR) detections – Confirm that EDR is detecting cyber threats such as malware.
Example:
To take one scenario from the above list, let us consider the testground for Cloud-delivered protection demonstration.
Cloud-delivered protection for Microsoft Defender Antivirus, also referred to as Microsoft Advanced Protection Service (MAPS), provides you with strong, fast protection in addition to our standard real-time protection.
Pre-requisites and Set-Up
- This will easily work with the Trial license that we learnt in my blog here : MDE Series-Part 8: Microsoft Defender for Endpoint Capabilities – cubic solutions GmbH.
- Windows 11, Windows 10, Windows 8.1, and Windows 7 SP1
- Microsoft Defender Real-time protection is enabled-It is enabled by default when the Onboarding takes place.
- Cloud-delivered protection is enabled by default during the onboarding of Windows device to Microsoft defender for Endpoint, however you may need to re-enable it if it has been disabled as part of previous organizational policies. For more information, see Enable cloud-delivered protection in Microsoft Defender Antivirus.
- See below snapshots from the Test device for reference:
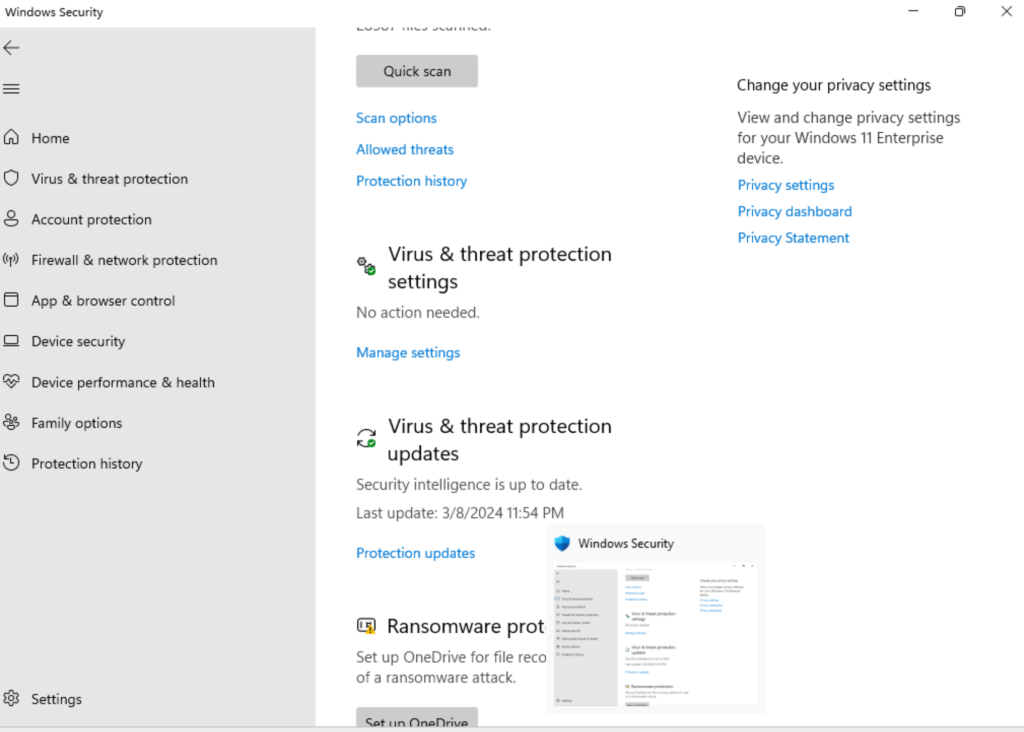
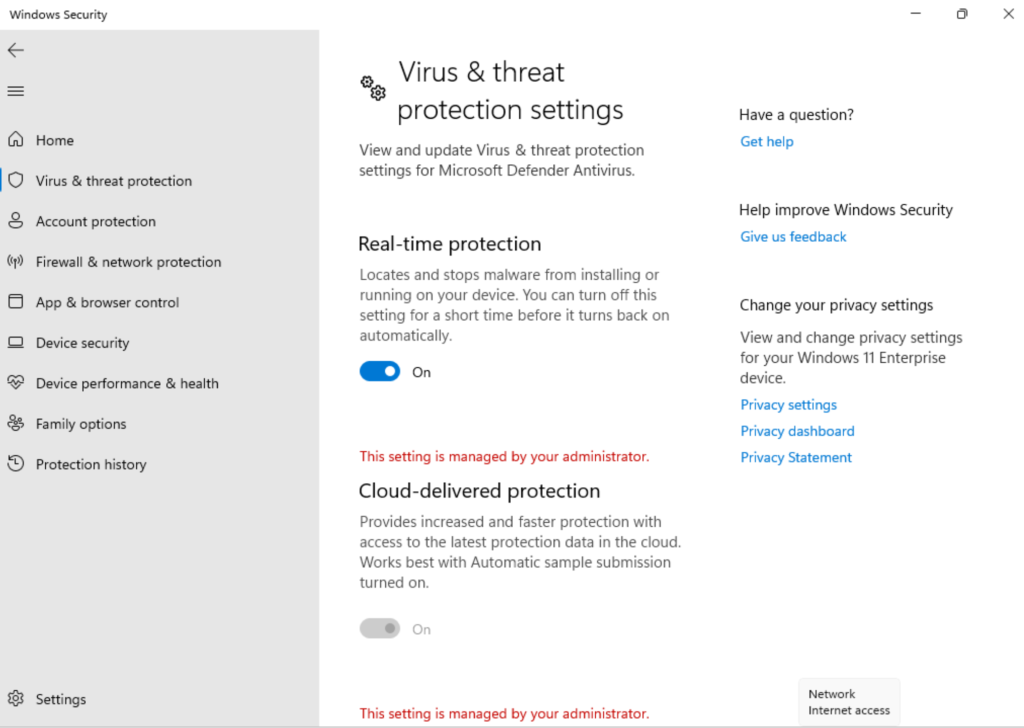
Steps:
- Download the test file. Important: The test file isn’t malicious, it’s just a harmless file simulating a virus. If you see file blocked by Microsoft Defender SmartScreen, select on “View downloads” button.
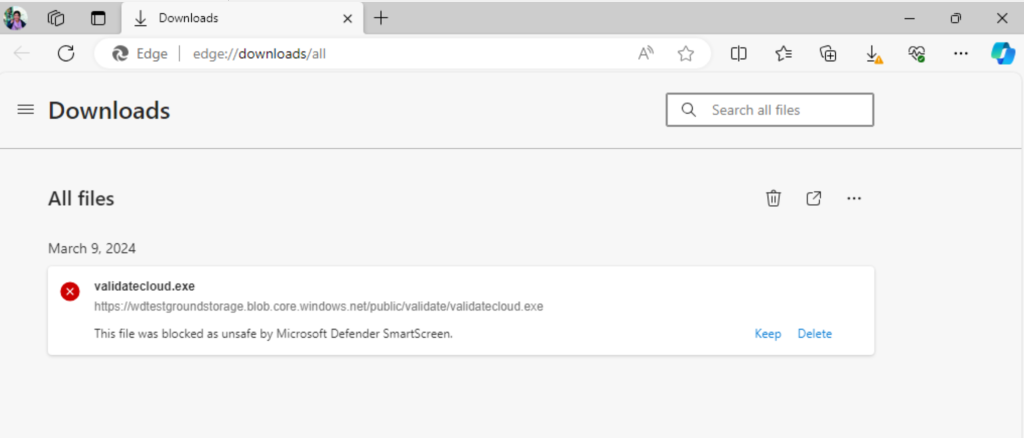
- In Downloads menu right select on the blocked file and select on Keep anyway.
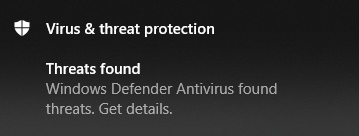
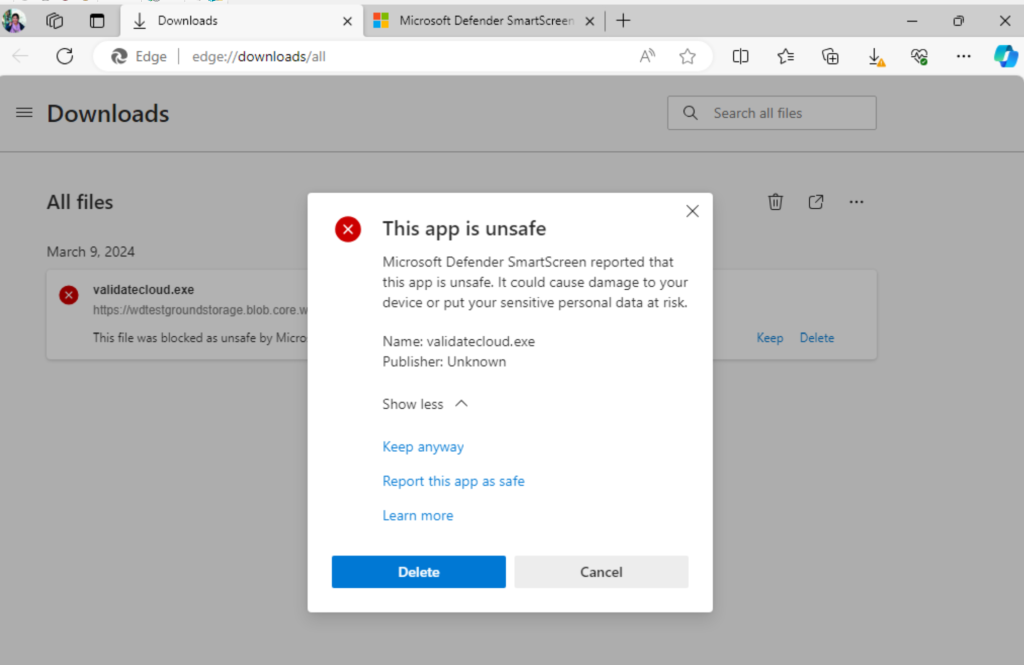 3. You should see that “Microsoft Defender Antivirus” found a virus and deleted it.
3. You should see that “Microsoft Defender Antivirus” found a virus and deleted it.

Note: In some cases, you might also see Threat Found notification from Microsoft Defender Security Center.
- If the file executes, or if you see that it was blocked by Microsoft Defender SmartScreen, cloud-delivered protection isn’t working. For more information, see Configure and validate network connections for Microsoft Defender Antivirus.Example:
Failed to block (but stopped by Microsoft Defender SmartScreen)
I encourage you to test these demonstrations for your Windows machine . This will help you gain more confidence to work and implement in a real-time scenario. Finally, with this Part-10 of the blog, we reach to the end of the Microsoft Defender for Endpoint Series .
Moreover, would you want to go to the other topics and revise? Well, here you goooo!
- Part 1: Microsoft Defender for Endpoint Series-Introduction
- Part 2: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint-In detail
- Part 3: Microsoft Defender for Endpoint Series- Integration of Microsoft Intune with Microsoft Defender for Endpoint
- Part 4: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint Onboarding Process using Microsoft Intune for Windows
- Part-5: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint Offboarding Process using Microsoft Intune
- Part 6: Microsoft Defender for Endpoint Series- Policy Creation to Set Device-Risk Level for Microsoft Defender for Endpoint
- Part 7: Microsoft Defender for Endpoint Series-Threat and Vulnerability Management
- Part 8: Microsoft Defender for Endpoint Series-Microsoft Defender for Endpoint Capabilities
- Part 9: Microsoft Defender for Endpoint Series-Microsoft Threat and Vulnearbility Management Capabilities
- Microsoft Defender Vulnerability Management | Microsoft Learn
- Manage endpoint vulnerabilities with Microsoft Defender Vulnerability Management – Training | Microsoft Learn
- Manage device discovery and vulnerability assessment – Training | Microsoft Learn
- Reduce your threat and vulnerability exposure – Training | Microsoft Learn
- Microsoft Defender Vulnerability Management dashboard | Microsoft Learn
- Microsoft Defender Vulnerability Management Blog – Microsoft Community Hub
My Motto is- ‘The Fastest Way To Learn & Retain Any Skill Is -To Teach It !’
Lastly, we recommend to Stay tuned with us for more such detailed insights on the known topics as well as new and trending issues. This is just the beginning.🌟
Author: Salona Sahni Kapoor aka Intunesiastic
cubic solutions GmbH
