Microsoft Defender for Endpoint Offboarding Process using Microsoft Intune
Do you often find forums discussing Microsoft Defender for Endpoint and its features, but still have questions in mind?
🚀A one-stop solution for all your questions- We have started a Microsoft Defender for Endpoint Series, where we want to cover topics on a deeper level and discover the possibilities with all kinds of threats and endpoints!
- Learn Microsoft Defender for Endpoint with #Salona aka #Intunesiastic
As seen in my earlier blogs from the Microsoft Defender for Endpoint Series, Microsoft Defender for Endpoint Series-Part 3 and Microsoft Defender for Endpoint Series-Part 4, we have already learnt to integrate Microsoft Intune and Microsoft Defender for Endpoint and onboarding of a Windows device to Microsoft Defender for Endpoint using Microsoft Intune.
Today Let’s learn Microsoft Defender for Endpoint Offboarding Process also using Microsoft Intune for the Windows platform.
Offboarding a device causes the device to stop sending data to Defender for Business. However, data received prior to offboarding is retained for up to six (6) months. These below points have to be taken care of well in advance before you perform the Offboarding:
Please Note:• The status of a device will be switched to Inactive 7 days after offboarding.• Offboarded devices’ data (such as Timeline, Alerts, Vulnerabilities, etc.) will remain in the portal until the configured retention period expires. Data from Microsoft Defender for Endpoint is retained for 180 days, visible across the portal. However, in the advanced hunting investigation experience, it’s accessible via a query for a period of 30 days. For more information on this, please refer to : retention period.• The device’s profile (without data) will remain in the Devices List for no longer than 180 days.• In addition, devices that are not active in the last 30 days are not factored in on the data that reflects your organization’s Defender Vulnerability Management exposure score and Microsoft Secure Score for Devices.• To view only active devices, you can filter by sensor health state, device tags or machine groups.
Registery Key for the Windows device onboarded to Microsoft Defender for Business
Offboarding Windows Devices from Mcirosoft Defender for Business using Microsoft Intune Earlier, like we had discussed about several methods available for Onboarding Windows devices , similarly, there are 3 methods available for Offboarding. These are:
- Offboard devices using a local script
- Offboard devices using Group Policy
- Offboard devices using Mobile Device Management tools
Now I would like to mention here in detail my personal favorite method- Yes, you guessed it right- It is Microsoft Intune!
The steps for Offboarding Windows device from MicrosoftDefender for Business using Microsoft Intune are :
Navigate to the Defender Portal at : to security.microsoft.com
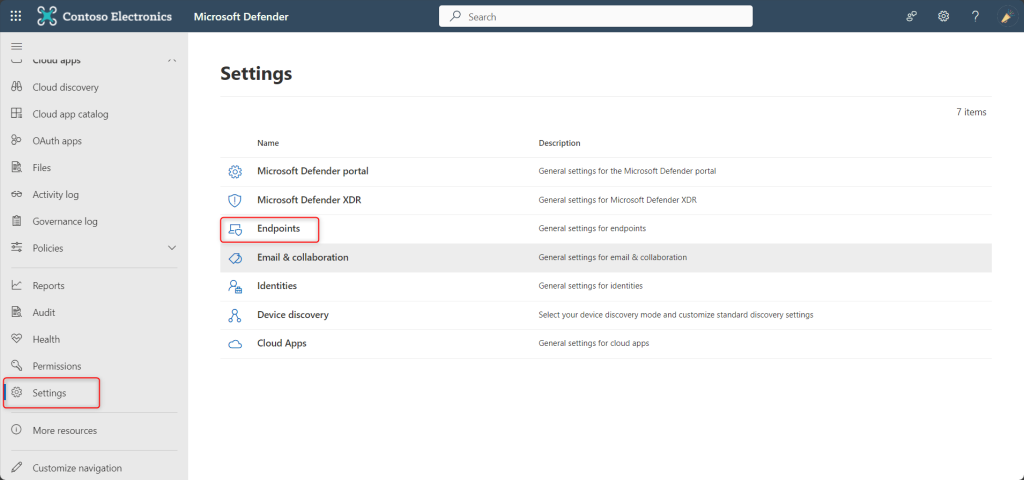
Click on Settings, select Endpoints
Scroll down and select Offboarding and mention other Menu settings as as shhown below. Click on ‘Download Package‘ to download a zip file that contains a file called WindowsDefenderATP_valid_until_YYYY-MM-DD.offboarding.
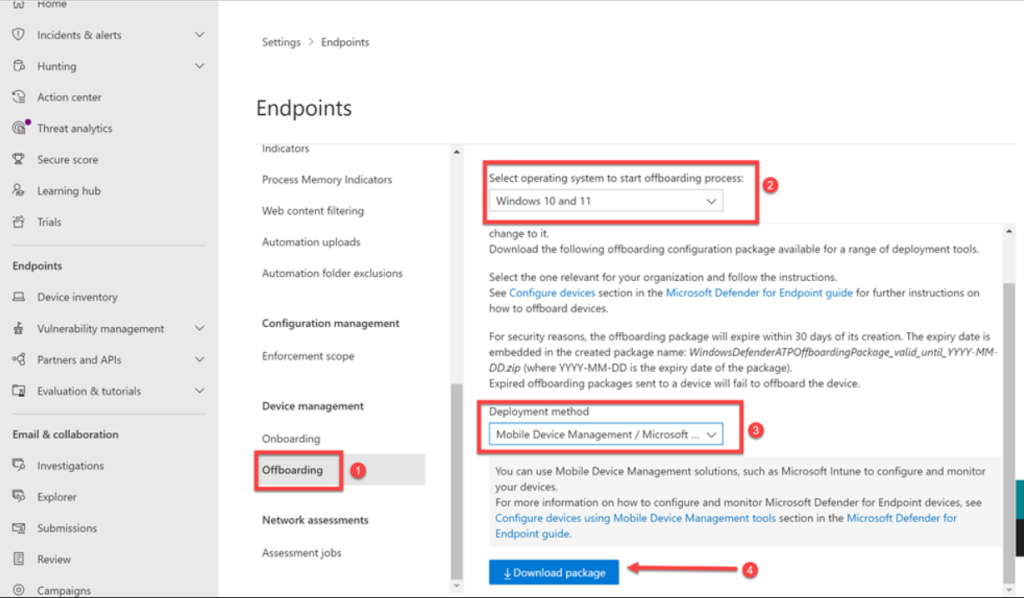
For security reasons, the package used to Offboard devices will expire 30 days after the date it was downloaded. Expired offboarding packages sent to a device will be rejected. That expiry date will be contained in the filename (here it is 1st March 2024) as shown below:
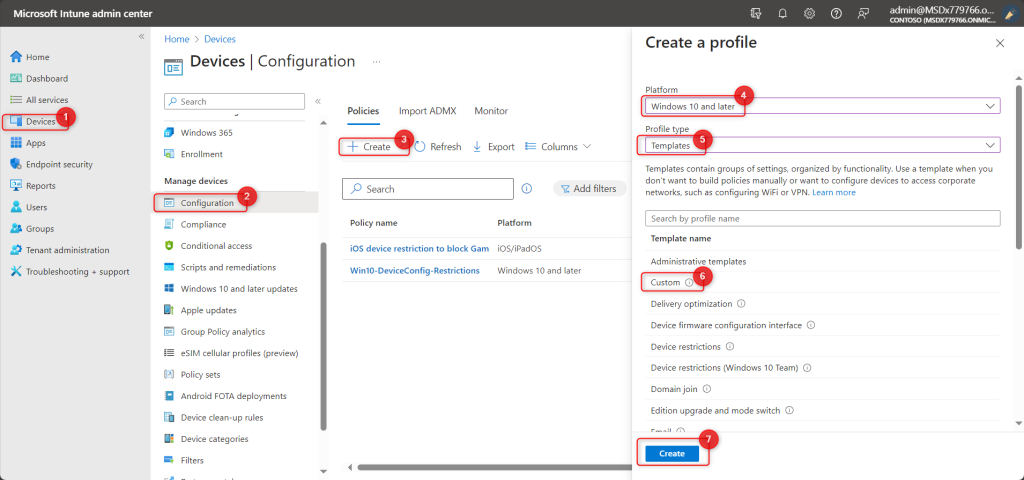
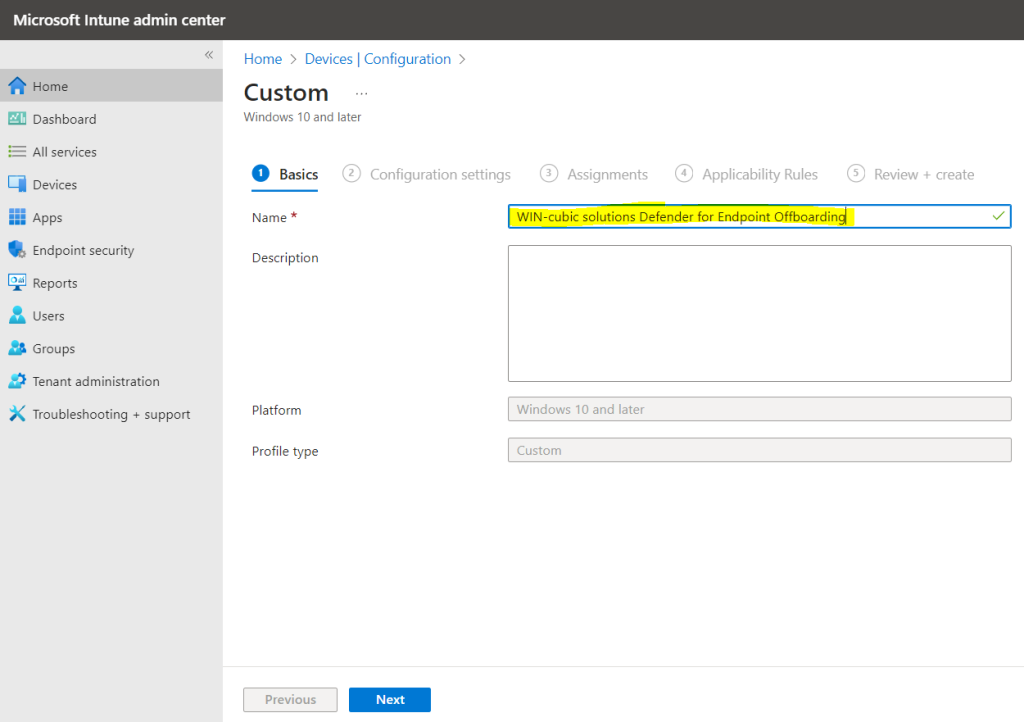
Now, navigate back to Microsoft Endpoint Manager and select Devices | Configuration profiles, then Create a Profile for Windows 10 or Later Platform, with Template Profile Type and Custom as the Template Name, click on Create. Give a Name and Description (optional) to this profile and Click on Next.
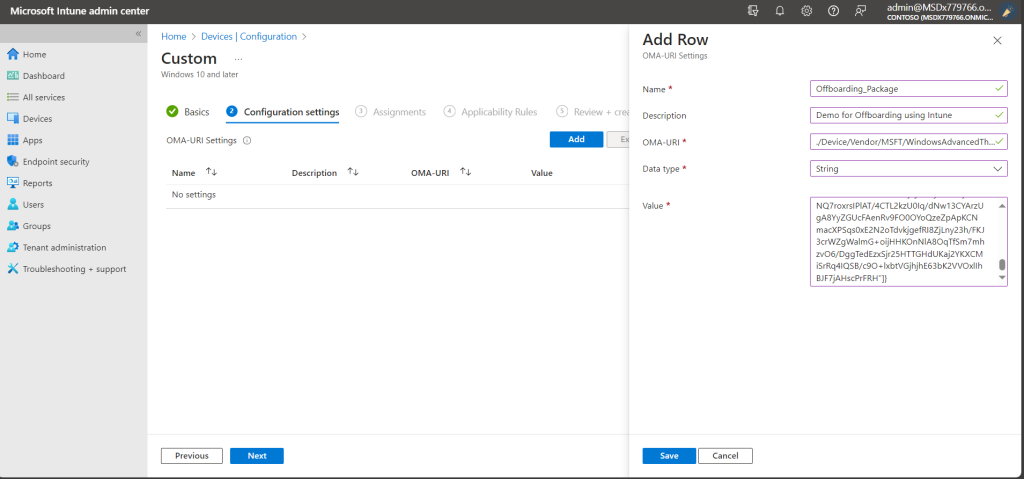
In Microsoft Intune custom configuration policy,enter the following OMA-URI settings.
- Name = <unique name> eg.Offboarding_Package and Description (optional)
- OMA-URI: ./Device/Vendor/MSFT/WindowsAdvancedThreatProtection/Offboarding
- Date type: String
- Value: [Copy and paste the value from the content of the WindowsDefenderATP_valid_until_YYYY-MM-DD.offboarding file]
Then, Click on Save.
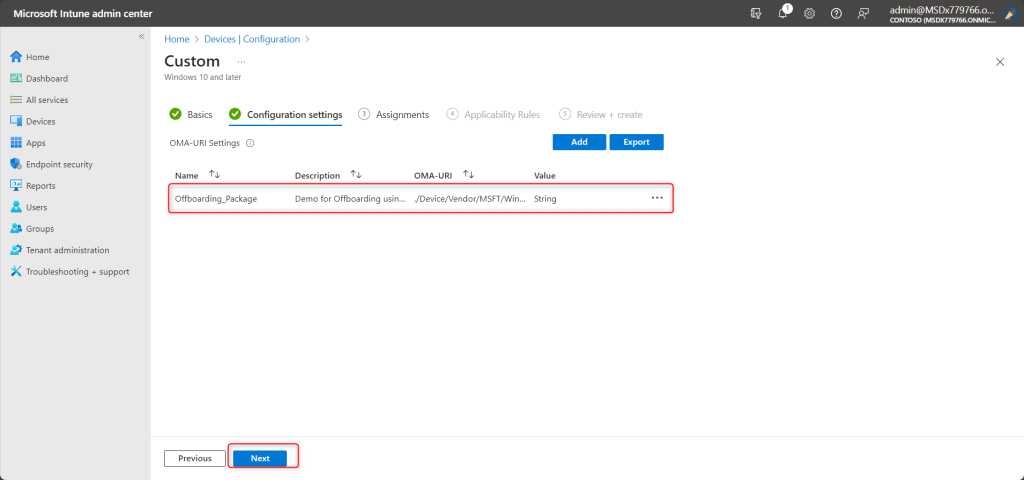
Then, Click on Next.
Then, Click on Next.
On the Assignments page, select the groups that will receive this profile. Select Next.
On the Review + create page, when you’re done, select Create. The new profile is displayed in the list when you select the policy type for the profile you created. Select OK, and then select Create to save your changes. At this point, the profile has been created.
Please Note: Onboarding and offboarding policies must not be deployed on the same device at the same time, otherwise this will cause unpredictable collisions. Also, it is not recommended to offboard all your devices at the same time from Defender for Endpoint.
Thereby, it is adavised to create a Dynamic Group in Microsoft Entra ID which has only those devices that you wish to Offboard.
For more inforation on Dynamic Groups, please refer to : Create or edit a dynamic group and get status – Microsoft Entra ID | Microsoft Learn
To check the Offboarding status of the Device, Click on the Device Status (of the Configuration Profile) created. Here you will see whether the policy has been successfully applied to the devices.
So now you may ask the most awaited question, Hey Salona aka #Intunesisatic, How long does it take for the policy to take effect?
The answer is not easy and it truly depends onmany factors when the devices ‘check in’ to receive the policy.
As mentioned earlier, ofcourse you could check the registry key, to confirm whether the the device has successfully been offboarded here: HKLM:\Software\Microsoft\Windows Advanced Threat Protection\Status\OnboardingState and ensure that it is equal to 0.
Please Note:
The device shall continue to be displayed in the Defender for Endpoint unless you use a display filter. In case you wish to offboard more devices, you just need to add them to the group you created and had assigned the configured the offboarding Intune Offboarding configuration policy .Also, it is important to know that, after 30 days you’ll need to go and download a new offboarding package from the Defender for Endpoint console and upload the contents of the new WindowsDefenderATP_valid_until_YYYY-MM-DD.offboarding file to the offboarding Intune policy to allow devices to be successfully offboarded going forward. However, you can leave the policy in place and simply update it as and when needed.
References:
- Offboard a device from Microsoft Defender for Business | Microsoft Learn
- Offboard devices | Microsoft Learn
Hence, I hope that today I have been able to give you a step-wise approach to Offboard Windows Devices from Microsoft Defender for Business with with Microsoft Intune. Moreover, would you want to go to the previous topics and revise? Well, here you goooo!
- Part 1: Microsoft Defender for Endpoint Series-Introduction
- Part 2: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint-In detail
- Part 3: Microsoft Defender for Endpoint Series- Integration of Microsoft Intune with Microsoft Defender for Endpoint
- Part 4: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint Onboarding Process using Microsoft Intune for Windows
- Part-5: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint Offboarding Process using Microsoft Intune
- Part 6: Microsoft Defender for Endpoint Series- Policy Creation to Set Device-Risk Level for Microsoft Defender for Endpoint
- Part 7: Microsoft Defender for Endpoint Series-Threat and Vulnerability Management
- Part 8: Microsoft Defender for Endpoint Series-Microsoft Defender for Endpoint Capabilities
- Part 9: Microsoft Defender for Endpoint Series-Microsoft Threat and Vulnearbility Management Capabilities
- Part 10: Microsoft Defender for Endpoint Series-Microsoft Defender for Endpoint Testground
Also, I strongly believe that – ‘The fastest way to learn and retain a skill is, to teach it!‘
Lastly, we recommend to stay tuned with us to progress on Microsoft Defender for Endpoint Chronicles. This is just the beginning.🌟
Author: Salona Sahni Kapoor aka Intunesiastic
cubic solutions GmbH
