Do you often find forums discussing Microsoft Defender for Endpoint and its features, but still have questions in mind?
🚀A one-stop solution for all your questions- We have started a new series where we want to cover topics on a deeper level and discover the possibilities with all kinds of threats and endpoints!
🔐Scenario -How Microsft Defender alongwith Microsoft Intune actually protects my Endpoint?
So right after my first blog Microsoft Defender for Endpoint Series-Part 1, I have been asked about real-life scenarios by Admins. Here is one: For this example, the following settings are pre-configured:
- Microsoft Defender for Endpoint and Intune are already integrated.
- The organization has an Intune device compliance policy that classifies devices with a Medium or High level of risk as noncompliant.
- The conditional access policy is configured to Block access.
Consider an event where someone sends a Word attachment with embedded malicious code to a user within your organization.
- The user opens the attachment, which enables the embedded code.
- An elevated privilege attack starts. An attacker from a remote machine has admin rights to the victim’s device.
- The attacker then remotely accesses the user’s other devices. This security breach can affect the entire organization.
Microsoft Defender for Endpoint can help resolve security events like this scenario.
- In this example, Microsoft Defender for Endpoint detects each of the actions that occurred:
- The device executed abnormal code.
- The device experienced a process privilege escalation.
- Malicious code was injected into the device.
- A suspicious remote shell was issued.
- Based on the actions from the device, Microsoft Defender for Endpoint classifies the device as high-risk. It also includes a detailed report of suspicious activity in the Microsoft Defender Security Center portal.
As such, the compromised device in this example is classified as noncompliant. This classification allows your conditional access policy to kick in and block access from that device to your corporate resources.
👉Platforms for Microsoft Defender for Endpoint ?
- Microsoft Defender for Endpoint on Windows
- Defender for Endpoint on Android
- Microsoft Defender for Endpoint on iOS
- Microsoft Defender for Endpoint on macOS
- Microsoft Defender for Endpoint on Linux
- Microsoft Defender for Endpoint on Servers
🔐Microsoft Defender for Endpoint deployment
The below diagram helps to identify your environment architecture, select the type of deployment tool that best fits your needs.
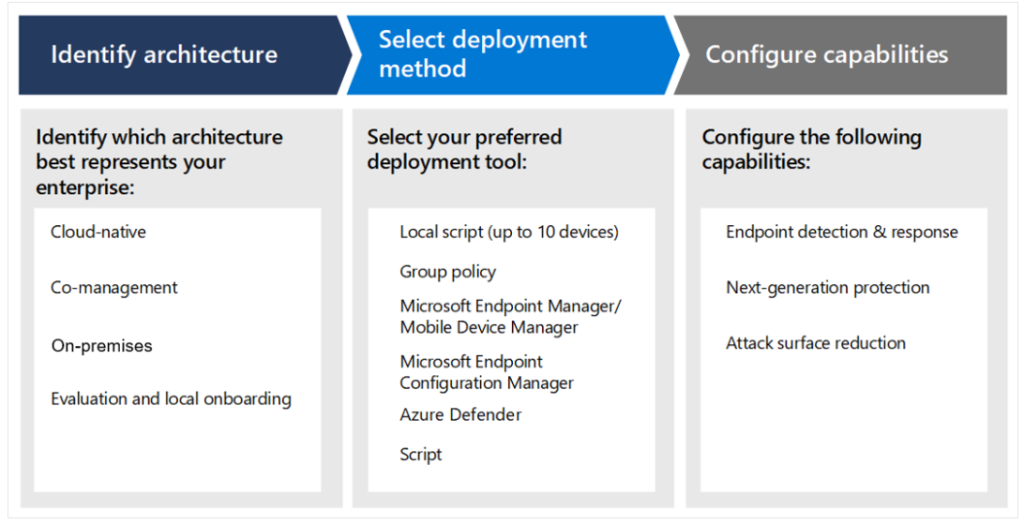
Microsoft Defender for Endpoint Deployment Methods
Step 1: Identify your environment
| Architecture | Description |
| Cloud-native | You are a cloud-native organization if you use Microsoft Intune as the management solution |
| Co-management | You use Config Manager (SCCM) and Microsoft Intune, both as the management solutions. |
| On-premises | You use Config Manager (SCCM) as the management solution. |
| Evaluation and local onboarding | This architecture is recommended by Microsoft for SOCs (Security Operations Centers) that are looking to evaluate or run a Microsoft Defender for Endpoint pilot, but don’t have existing management or deployment tools. This architecture can also be used to onboard devices in small environments without management infrastructure, such as a DMZ (Demilitarized Zone) |
Step 2: Select deployment method
| Endpoint | Deployment tool |
| Windows |
Local script (up to 10 devices) Microsoft Intune/ Mobile Device Manager |
| Android | Microsoft Intune |
| iOS | |
| macOS | Local script Microsoft Intune JAMF Pro Mobile Device Management |
|
Windows servers Linux servers |
Integration with Microsoft Defender for Cloud |
| Linux servers | Local script Puppet Ansible Chef Saltstack |
As seen in above table, Microsoft Intune is the most common methods of deployment among- Windows, Android, iOS and macOS platforms.
I hope that today we have taken a 2nd step towards the understanding of Microsoft Defender for Endpoint.
Moreover, would you want to go to the next steps and learn more? Here you goooo!
- Part 1: Microsoft Defender for Endpoint Series-Introduction
- Part 2: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint-In detail
- Part 3: Microsoft Defender for Endpoint Series- Integration of Microsoft Intune with Microsoft Defender for Endpoint
- Part 4: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint Onboarding Process using Microsoft Intune for Windows
- Part-5: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint Offboarding Process using Microsoft Intune
- Part 6: Microsoft Defender for Endpoint Series- Policy Creation to Set Device-Risk Level for Microsoft Defender for Endpoint
- Part 7: Microsoft Defender for Endpoint Series-Threat and Vulnerability Management
- Part 8: Microsoft Defender for Endpoint Series-Microsoft Defender for Endpoint Capabilities
- Part 9: Microsoft Defender for Endpoint Series-Microsoft Threat and Vulnearbility Management Capabilities
- Part 10: Microsoft Defender for Endpoint Series-Microsoft Defender for Endpoint Testground
I strongly believe that- ‘The Fastest Way To Learn & Retain Any Skill Is -To Teach It !’
Stay tuned if you want to learn more, this is just the beginning.🌟
Author: Salona Sahni Kapoor aka Intunesiastic
cubic solutions GmbH
