Microsoft Defender for Endpoint Capabilities
Do you often find forums discussing Microsoft Defender for Endpoint and its features, but still have questions in mind?
🚀A one-stop solution for all your questions- We have started a Microsoft Defender for Endpoint Series, where we want to cover topics on a deeper level and discover the possibilities with all kinds of threats and endpoints!
Fig i) Learn Microsoft Defender for Endpoint with #Salona aka #Intunesiastic
In the previous blog, we have already learnt a brief about one of the capabilities of Microsoft Defender for Endpoint which is -Microsoft’s Threat and Vulnerability Management. Let us get to know some more of these today. I shall also share a summary of vulnerability management capabilities and how to apply for it’s trial plan .
After onboarding the devices, you need to configure the other capabilities of Microsoft Defender for Endpoint.
Onboarding devices effectively enables the endpoint detection and response (EDR) capability of Microsoft Defender for Endpoint. In many cases, organizations will have existing endpoint security products in place. The bare minimum being an antivirus solution, but in some cases, an organization might have existing EDR solution.
It is common that Defender for Endpoint will need to exist along side these existing endpoint security products either indefinitely or during a cutover period. Fortunately, Defender for Endpoint and the endpoint security suite is modular and can be adopted in a systematic approach.
The following table lists the capabilities & their order in which these should be configured to get the best protection for the organization:
|
Capability |
Description |
Adoption Order Rank |
|
Endpoint Detection & Response (EDR)
|
Defender for Endpoint endpoint detection and response capabilities provide advanced attack detections that are near real-time and actionable. Security analysts can prioritize alerts effectively, gain visibility into the full scope of a breach, and take response actions to remediate threats.
|
1 |
|
Configure Microsoft Defender Vulnerability Management
|
Defender Vulnerability Management is a component of Microsoft Defender for Endpoint, and provides both security administrators and security operations teams with unique value, including: – Real-time endpoint detection and response (EDR) insights correlated with endpoint vulnerabilities. – Invaluable device vulnerability context during incident investigations. – Built-in remediation processes through Microsoft Intune and Microsoft System Center Configuration Manager.
|
2 |
|
Configure Next-generation protection (NGP)
|
Microsoft Defender Antivirus is a built-in antimalware solution that provides next-generation protection for desktops, portable computers, and servers. Microsoft Defender Antivirus includes: -Cloud-delivered protection for near-instant detection and blocking of new and emerging threats. Along with machine learning and the Intelligent Security Graph, cloud-delivered protection is part of the next-gen technologies that power Microsoft Defender Antivirus. – Always-on scanning using advanced file and process behavior monitoring and other heuristics (also known as “real-time protection”). – Dedicated protection updates based on machine learning, human and automated big-data analysis, and in-depth threat resistance research.
|
3 |
|
Configure attack surface reduction>
|
Attack surface reduction capabilities in Microsoft Defender for Endpoint help protect the devices and applications in the organization from new and emerging threats. |
4 |
|
Configure Auto Investigation & Remediation (AIR) capabilities
|
Microsoft Defender for Endpoint uses Automated investigations to significantly reduce the volume of alerts that need to be investigated individually. The Automated investigation feature leverages various inspection algorithms, and processes used by analysts (such as playbooks) to examine alerts and take immediate remediation action to resolve breaches. This significantly reduces alert volume, allowing security operations experts to focus on more sophisticated threats and other high value initiatives.>
|
Not applicable |
|
Configure Microsoft Defender Experts capabilities
|
Microsoft Experts is a managed hunting service that provides Security Operation Centers (SOCs) with expert level monitoring and analysis to help them ensure that critical threats in their unique environments don’t get missed.
|
Not applicable |
Onboard/Offboard to Microsoft Defender Vulnerability Management
Furthermore extensipon to my previous blog, let us now discuss a little more in detail about Threat and Vulnerabilty Management . To onboard devices to Defender Vulnerability Management you need not follow any specific steps. You have already performed onboarding of Windows device to Microsoft Defender for Endpoint and that’s it. The process to Offboard is also the same as that of Offboarding fromMicrosoft Defender for Endpoint.
Microsoft Defender Vulnerability Management Add-On Trial plan
To sign up for the Defender Vulnerability Management trial, you can go directly to the Microsoft 365 trials hub page or by selecting Trials on the left navigation from the Microsoft Defender 365 portal.
- If you have Defender for Endpoint Plan 2, find the Defender Vulnerability Management add-on card and select Try now.
- If you’re a new customer or an existing Defender for Endpoint P1 or Microsoft 365 E3 or Microsoft 365 E5 customer, choose the Defender Vulnerability Management card and select Try now.In the below picture, as I had already click on Try Now, it shoes as Active as highlighted.
- Review the information about what’s included in the trial, then select Begin trial. Your trial will be effective immediately:The Defender Vulnerability Management add-on trial lasts for 90 days.
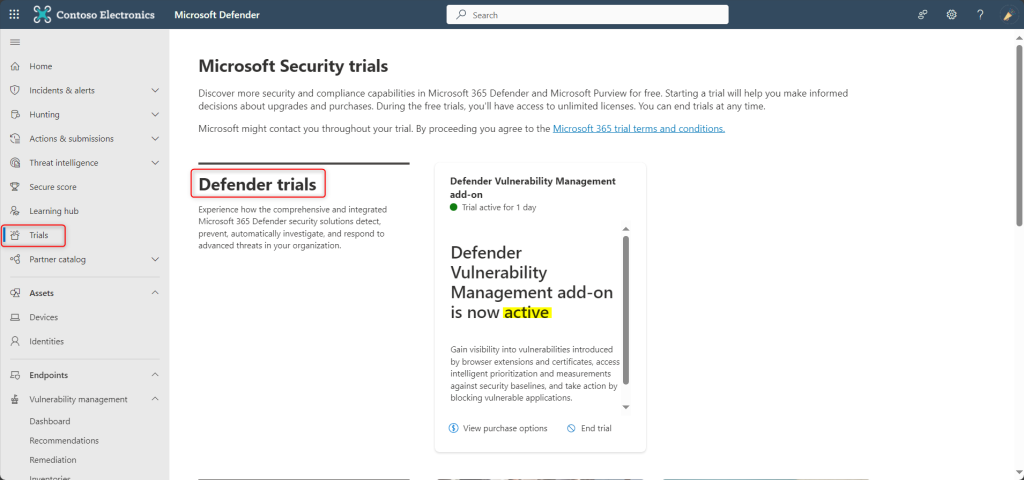
It can take up to 6 hours for all vulnerability management features to appear in your left navigation. Sign out and sign back in to see the updates.
As a Global Administrator, you can start the trial or you can allow to users start the trial on behalf of your organization.
As part of the trial setup, the new Defender Vulnerability Management trial licenses will NOT be applied to users automatically. Therefore, you need to specifically assign the license to end-user. The licenses are active for the duration of the trial. In the below snapshot, I shall be assigning the Defender Vulnerability Management trial license separately to the end-user.
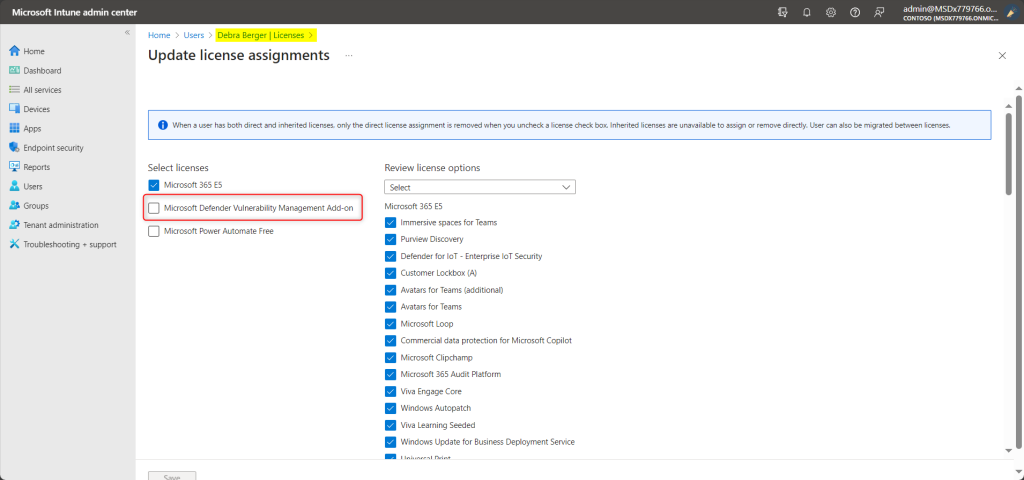
Getting Started
You can start using Defender Vulnerability Management features as soon as you see them in the Microsoft Defender portal. Nothing is created automatically and users won’t be affected. When you navigate to each solution, you may be guided to make extra setup configurations to start using features.
Extending the trial
You can extend the trial within the last 15 days of the trial period. You’re limited to a maximum of two trial periods. If you don’t extend by the time your trial period ends, you’ll need to wait at least 30 days before signing up for a second trial.
Admins can disable the trial anytime by selecting Trials on the left navigation, going to the Defender Vulnerability Management trial card and selecting End trial.
Unless stated otherwise for the solution your trial data will be maintained for time, usually 180 days, before being permanently deleted. You may continue to access the data gathered during the trial until that time.
Microsoft Defender Vulnerability Management Capabilities
The free Defender Vulnerability Management trial includes:
- Security baselines assessment: When the trial ends security baseline profiles may be stored for a short additional time before being deleted.
- Blocking vulnerable applications: When the trial ends blocked applications will be immediately unblocked whereas baseline profiles may be stored for a short additional time before being deleted.
- Browser extensions assessment
- Digital certificates assessment
- Network shares analysis
- Hardware and firmware assessment
- Authenticated scan for Windows
So, I hope that today, I was able to simplify your understanding on the capabilities of Microsoft Defender for Endpoint and Threat and Vulnerability Management module .
Moreover, would you want to go to the other topics and revise? Well, here you goooo!
- Part 1: Microsoft Defender for Endpoint Series-Introduction
- Part 2: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint-In detail
- Part 3: Microsoft Defender for Endpoint Series- Integration of Microsoft Intune with Microsoft Defender for Endpoint
- Part 4: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint Onboarding Process using Microsoft Intune for Windows
- Part-5: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint Offboarding Process using Microsoft Intune
- Part 6: Microsoft Defender for Endpoint Series- Policy Creation to Set Device-Risk Level for Microsoft Defender for Endpoint
- Part 7: Microsoft Defender for Endpoint Series-Threat and Vulnerability Management
- Part 9: Microsoft Defender for Endpoint Series-Microsoft Threat and Vulnearbility Management Capabilities
- Part 10: Microsoft Defender for Endpoint Series-Microsoft Defender for Endpoint Testground
- Microsoft Defender Vulnerability Management | Microsoft Learn
- Manage endpoint vulnerabilities with Microsoft Defender Vulnerability Management – Training | Microsoft Learn
- Manage device discovery and vulnerability assessment – Training | Microsoft Learn
- Reduce your threat and vulnerability exposure – Training | Microsoft Learn
- Microsoft Defender Vulnerability Management dashboard | Microsoft Learn
- Microsoft Defender Vulnerability Management Blog – Microsoft Community Hub
My Motto is- ‘The Fastest Way To Learn & Retain Any Skill Is -To Teach It !’
Lastly, we recommend to Stay tuned with us to progress on Microsoft Defender for Endpoint Chronicles. This is just the beginning.🌟
Author: Salona Sahni Kapoor aka Intunesiastic
cubic solutions GmbH
