Microsoft Threat and Vulnerability Management Capabilities
Do you often find forums discussing Microsoft Defender for Endpoint and its features, but still have questions in mind?
🚀A one-stop solution for all your questions- We have started a Microsoft Defender for Endpoint Series, where we want to cover topics on a deeper level and discover the possibilities with all kinds of threats and endpoints!
Fig i) Learn Microsoft Defender for Endpoint with #Salona aka #Intunesiastic
In the previous blog, we gained knowledge on the trial add-on licensing and capabilities of Microsoft’s Threat and Vulnerability Management in Microsoft Defender for Endpoint. I ensure that my blogs are thoroughly detailed for the beginners who would wish to learn Microsoft Defender for Endpoint from the scratch. Further nurturing this idea, my today’s blog brings you a Start-Up guide to Microsoft Threat and Vulnerability Management (TVM) that explains what all is available, what you need to set-up, which settings or policies you need to create, which configurations shall load by default, what and how to track and much more!
It’s time to Try Key Capabilities of Microsoft TVM
In order to to start using the Defender Vulnerability Management trial, visit the Microsoft Defender portal and select Vulnerability management in the left navigation bar.
It is important to note that the built-in and agentless scanners continuously monitor and detect risk even when devices aren’t connected to the corporate network. A singe view in TVM consolidates device inventory, software applications, browser extensions, digital certificates and hardware -firmware.
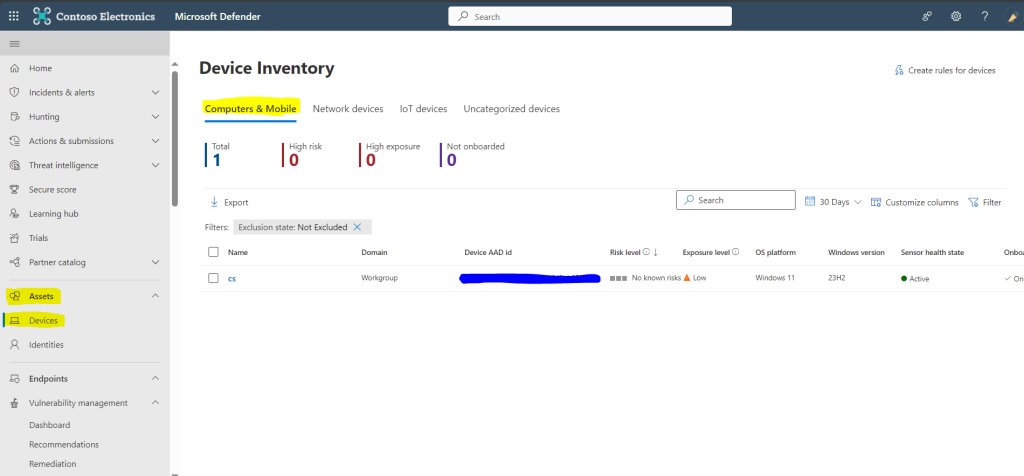
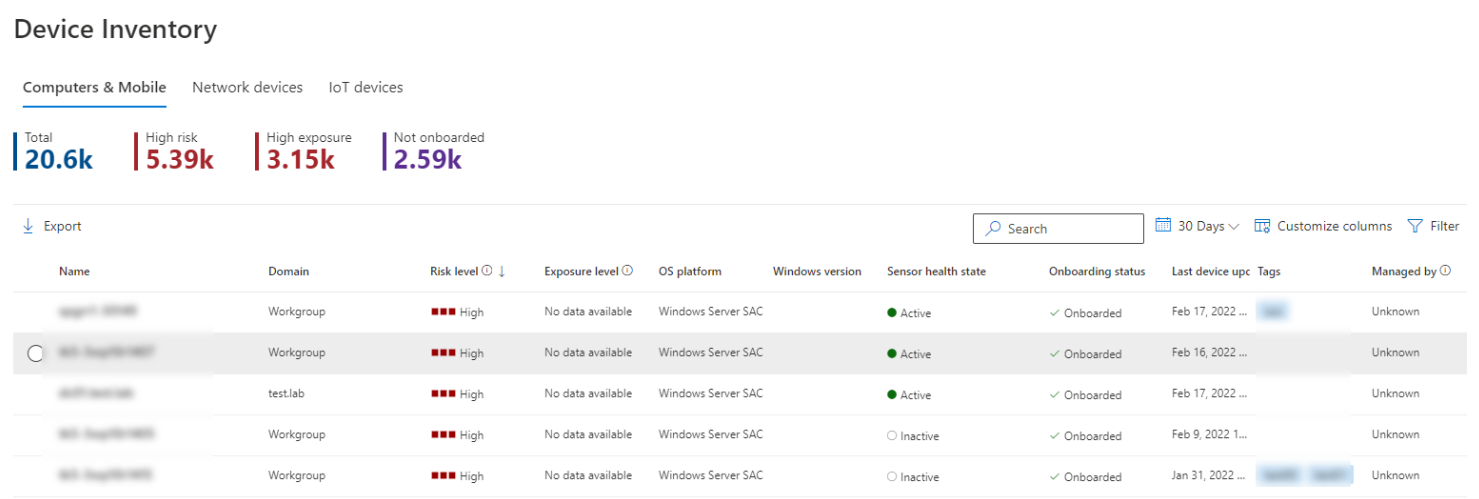
- Device inventory – On the DefenderPortal, Under Assets, Click on Devices. It shows a list of the devices seen in the last 30 days in your network. At a glance, you’ll see information such as device name, domain, risk level, exposure level, Tags, Device Value, Exclusion state, OS platform, First seen, Windows version, sensor health state, onboarding status, Antivirus status, Group, Managed by, Device Type, Mitigation status, associated CVEs, and other details for easy identification of devices most at risk. You can filter the inventory on this bases as well.During the Microsoft Defender for Endpoint onboarding process, devices onboarded to MDE are gradually populated into the device inventory as they begin to report sensor data. Following this, the device inventory is populated by devices that are discovered in your network through the device discovery process. The device inventory has three tabs that list devices as follows. By default, the device inventory opens on the Computers and Mobile tab.
- Computers and Mobile: Enterprise endpoints (workstations, servers, and mobile devices)
- Network devices: Devices like routers and switches
- IoT devices: Devices like printers and cameras
2. Software application inventory– This is a list of known applications in your organization. The view includes vulnerability and misconfiguration insights across installed software with prioritized impact scores and details such as OS platforms, vendors, number of weaknesses, threats, and an entity-level view of exposed devices.
Select the name of a device to open the device page (like Computer1), then select the Inventories tab to see a list of all the known software present on the device. Select a specific software entry to open the flyout with more information.
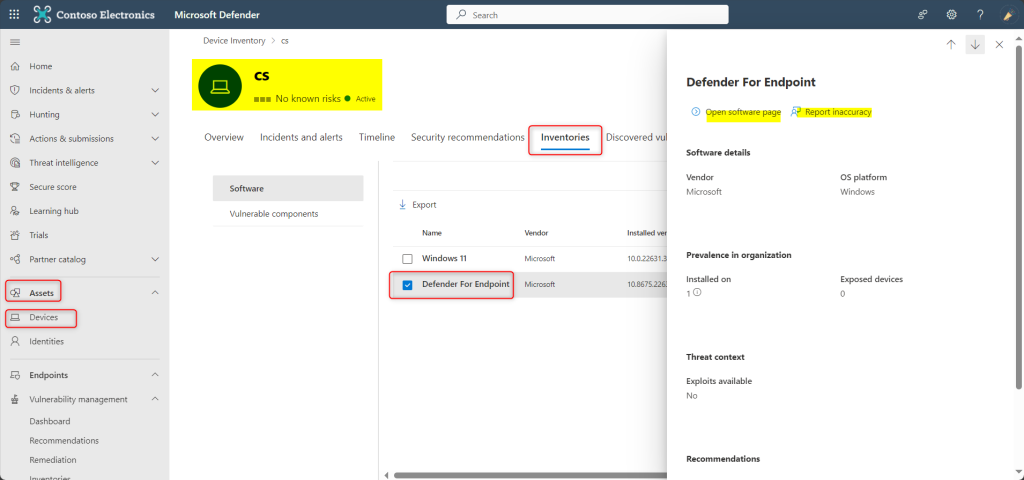
- Software may be visible at the device level even if it’s currently not supported by vulnerability management. However, only limited data will be available. You’ll know if software is unsupported because it will say “Not available” in the “Weakness” column.
- Software with no CPE can also show up under this device-specific software inventory.
- Report Inaccuracy : Report an inaccuracy when you see vulnerability information and assessment results that are incorrect. From the flyout pane, choose an issue to report from: a software detail is wrong OR the software is not installed on any device in my org OR the number of installed or exposed devices is wrong. Fill in the requested details about the inaccuracy and Submit. Your feedback is immediately sent to the vulnerability management experts.
- Software evidence: In reference to above snapshot, scroll down to Recommendations, you will see Impact and Software Evidence. See evidence of where we detected a specific software on a device from the registry, disk, or both. You can find it on any device in the device software inventory.
- Open Software Page :
A full page will appear with all the details of a specific software and the following information:- Side panel with vendor information, prevalence of the software in the organization (including number of devices it’s installed on, and exposed devices that aren’t patched), whether and exploit is available, and impact to exposure score.
- Data visualizations showing the number of, and severity of, vulnerabilities and misconfigurations. Also, graphs with the number of exposed devices.
- Tabs showing information such as:
- Corresponding security recommendations for the weaknesses and vulnerabilities identified.
- Named CVEs of discovered vulnerabilities.
- Devices that have the software installed (along with device name, domain, OS, and more).
- Software version list (including number of devices the version is installed on, the number of discovered vulnerabilities, and the names of the installed devices).
3. Browser extension assessments– A browser extension is a small software application that adds functionality to a web browser. The Browser extensions page displays a list of the browser extensions installed across different browsers in your organization. Extensions usually need different permissions to run properly. Visibility into the detailed information on the permissions requested for each installed extension, per browser- identifies those with the highest associated risk levels, the devices with the extension turned on, installed versions, the users who installed it and if it’s turned on or off on a device and more.
- Go to Vulnerability management > Inventories in the Microsoft Defender portal.
- Select the Browser extensions tab.The Browser extensions page opens with a list of the browser extensions installed across your organization.
- Extension Details : It has the details on the extension name, browser, the number of devices the extension is installed on, and the number that have it turned on as below:. The Requested permissions and Permissions risk columns provide more specific information on the number of permissions requested by the extension, and the permissions risk level based on the type of access to devices or sites it requested.
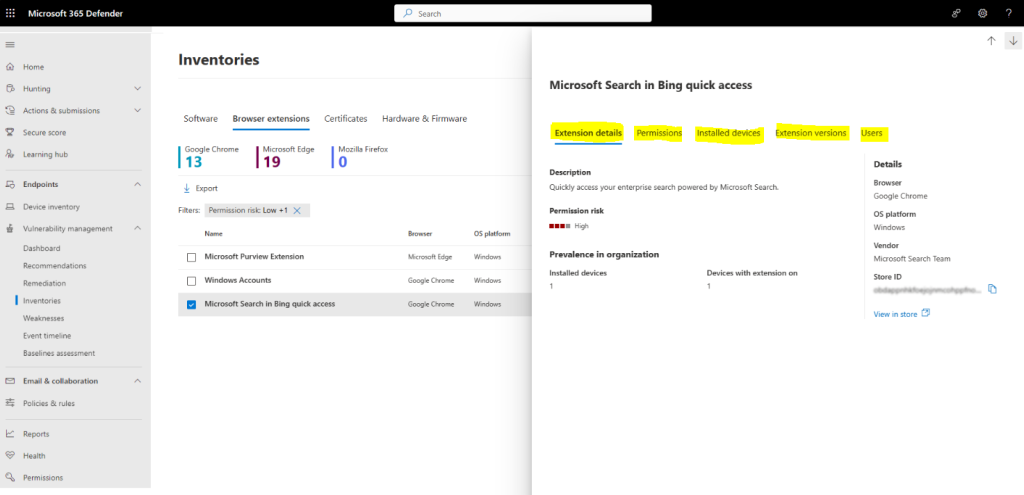
Browser extension permissions: Browser extensions usually need different types of permission to run properly, for example, they might require permission to modify a webpage. Select the Permissions tab, from the browser extension flyout pane, to see information on the permissions the browser extension needs to run, and whether this permission is optional or not. The permission risk level generated is based on the type of access the permission is requesting. You can use this information to help make an informed decision on whether you want to allow or block this extension.
View installed devices :To see the list of the devices the extension is installed on, choose the Installed devices tab from the browser extension flyout pane. From here, you can search for a particular device the extension is installed on, and you can export a list of the devices to a csv file.
View extension versions:Select the Extensions versions tab, from the browser extension flyout pane, to see information on the versions of the extension installed in your organization.
View extensions users: Select the Users tab, from the browser extension flyout pane, to see a list of users who installed the browser extension.
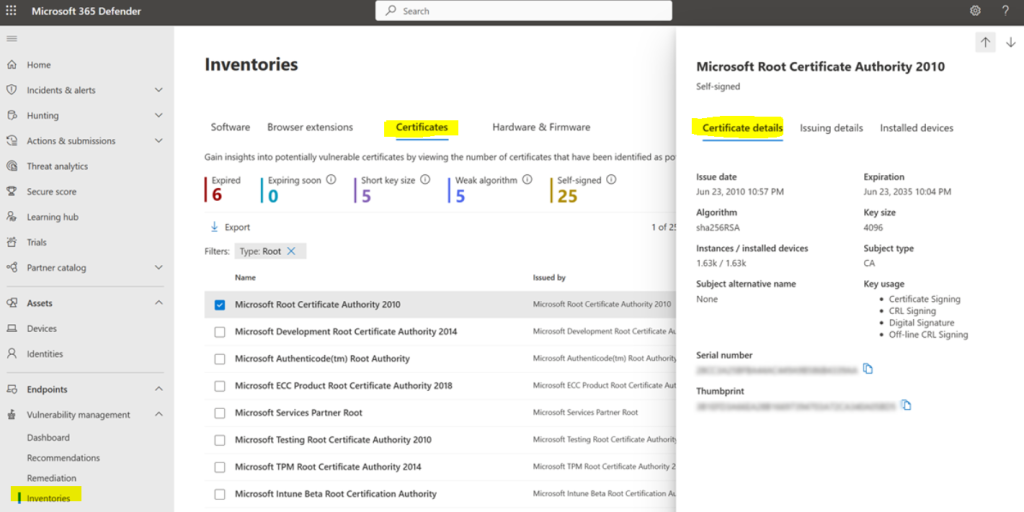
4. Certificate inventory – It allows you to discover, assess, and manage digital certificates installed across your organization in a single view. This can help you:
- Identify certificates that are about to expire so you can update them and prevent service disruption.
- Detect potential vulnerabilities due to the use of weak signature algorithm (for example, SHA-1-RSA), short key size (for example, RSA 512 bit), or weak signature hash algorithm (for example, MD5).
- Ensure compliance with regulatory guidelines and organizational policy.
- Go to Vulnerability management > Software inventory in the Microsoft Defender portal.
- Select the Certificates tab.
- The Certificate inventory page opens with a list of the certificates installed across your organization, including details on the expiration date, key size, who issued the certificate, and the number of instances.
5. Hardware and firmware – It provides a list of known hardware and firmware in your organization. It provides individual inventories for system models, processors, and BIOS. Each view includes details such as the name of the vendor, number of weaknesses, threats insights, and the number of exposed devices.
- Go to Vulnerability management > Inventories in the Microsoft Defender portal.
- Select the Hardware and Firmware tab.
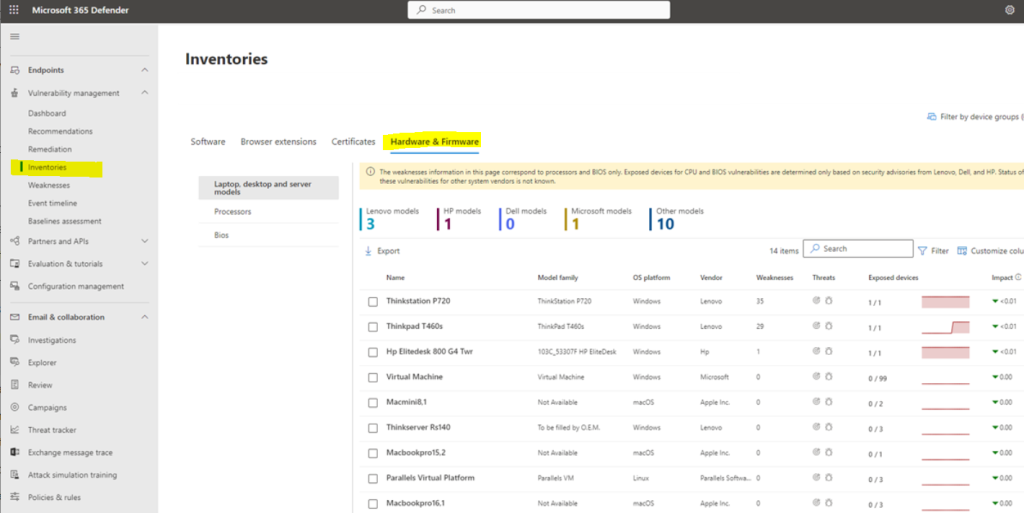
The Hardware and Firmware page opens with individual pages for:
- Laptop, desktop, and server models inventory
- Processor inventory- Select the Processors page to see a list of all processors in the organization. At the top of the page, you can view the number of processors per vendor.
- BIOS inventory-Select the BIOS page to view a list of all BIOS firmware in the organization.At the top of the page, you can view the number of BIOS per vendor.
6. Authenticated scan for Windows – with Authenticated scan for Windows you can remotely target by IP ranges or hostnames and scan Windows services by providing Defender Vulnerability Management with credentials to remotely access the devices. Once configured the targeted unmanaged devices will be scanned regularly for software vulnerabilities.
7. Assign device value – defining a device’s value helps you differentiate between asset priorities. The device value is used to incorporate the risk appetite of an individual asset into the Defender Vulnerability Management exposure score calculation. Devices assigned as “high value” will receive more weight. Device value options:
-
- Low
- Normal (Default)
- High
By this we come to the end of discussing the capabilities of Microsoft Threat and Vulnerability Management module . Hope this has made your understanding better in Microsoft Defender for Endpoint.
Moreover, would you want to go to the other topics and revise? Well, here you goooo!
- Part 1: Microsoft Defender for Endpoint Series-Introduction
- Part 2: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint-In detail
- Part 3: Microsoft Defender for Endpoint Series- Integration of Microsoft Intune with Microsoft Defender for Endpoint
- Part 4: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint Onboarding Process using Microsoft Intune for Windows
- Part-5: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint Offboarding Process using Microsoft Intune
- Part 6: Microsoft Defender for Endpoint Series- Policy Creation to Set Device-Risk Level for Microsoft Defender for Endpoint
- Part 7: Microsoft Defender for Endpoint Series-Threat and Vulnerability Management
- Part 8: Microsoft Defender for Endpoint Series-Microsoft Defender for Endpoint Capabilities
- Part 10: Microsoft Defender for Endpoint Series-Microsoft Defender for Endpoint Testground
- Microsoft Defender Vulnerability Management | Microsoft Learn
- Manage endpoint vulnerabilities with Microsoft Defender Vulnerability Management – Training | Microsoft Learn
- Manage device discovery and vulnerability assessment – Training | Microsoft Learn
- Reduce your threat and vulnerability exposure – Training | Microsoft Learn
- Microsoft Defender Vulnerability Management dashboard | Microsoft Learn
- Microsoft Defender Vulnerability Management Blog – Microsoft Community Hub
My Motto is- ‘The Fastest Way To Learn & Retain Any Skill Is -To Teach It !’
Lastly, we recommend to Stay tuned with us to progress on Microsoft Defender for Endpoint Chronicles. This is just the beginning.🌟
Author: Salona Sahni Kapoor aka Intunesiastic
cubic solutions GmbH
