Integration of Microsoft Intune with Microsoft Defender for Endpoint
Do you often find forums discussing Microsoft Defender for Endpoint and its features, but still have questions in mind?
🚀A one-stop solution for all your questions- We have started a Microsoft Defender for Endpoint Series, where we want to cover topics on a deeper level and discover the possibilities with all kinds of threats and endpoints!
- Learn Microsoft Defender for Endpoint with #Salona aka #Intunesiastic
Since seen in my second blog of the Microsoft Defender for Endpoint Series, Microsoft Defender for Endpoint Series-Part 2 Microsoft Intune is the most common methods of deployment among- Windows 10/11, Android, iOS and macOS platforms. So, let us first see, how to integrate Microsoft Intune with Microsoft Defender for Endpoint in these generic steps below:
- Establish a service-to-service connection between Intune & Microsoft Defender for Endpoint.-This connection lets Microsoft Defender for Endpoint collect data about machine risk from supported devices you manage with Intune.
- Use Intune policy to onboard devices with Microsoft Defender for Endpoint.-You onboard devices to configure them to communicate with Microsoft Defender for Endpoint and to provide data that helps assess their risk level.
- Use Intune device compliance policies to set the level of risk you want to allow.-Microsoft Defender for Endpoint reports a devices risk level. Devices that exceed the allowed risk level are identified as non-compliant.
- Use a conditional access policy.-to block users from accessing corporate resources from devices that are non-compliant.
- Use app protection policies (MAM).-For Android and iOS/iPadOS, to set device risk levels. App protection polices work with both enrolled and unenrolled devices.
🔐Integration of Microsoft Intune with Microsoft Defender for Endpoint
To set up the service-to-service connection between Intune and Microsoft Defender for Endpoint, you only need to enable Microsoft Defender for Endpoint a single time per tenant. These steps are as below:
- Navigate to the Microsoft Endpoint Manager admin center. Select Endpoint security in the navigation pane.
- On the Endpoint security | Overview page, under the Setup section in the navigation pane, select Microsoft Defender for Endpoint. Under the Microsoft Defender for Endpoint, you can see the Configuring Microsoft Defender for Endpoint.
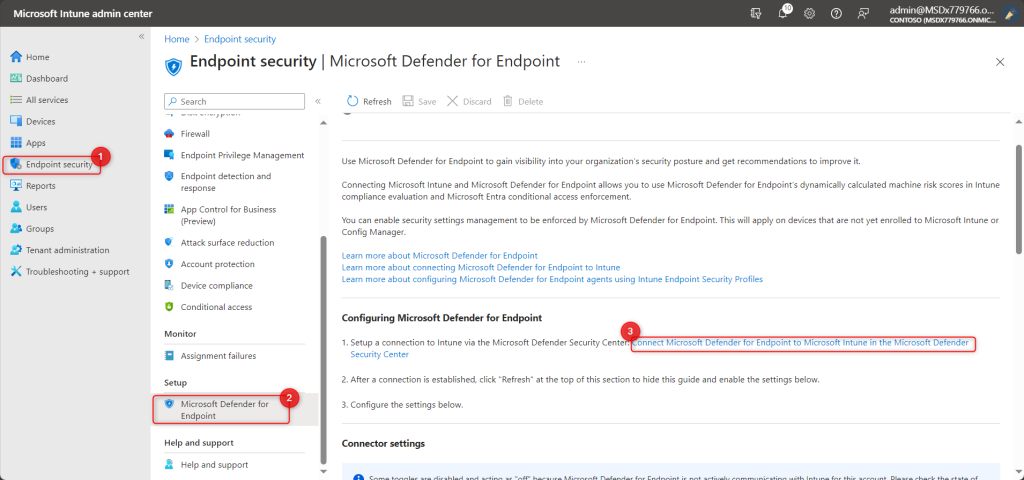
Fig1) Defender for Endpoint
- From the above window, click the link “Connect Microsoft Defender for Endpoint to Microsoft Intune in the Microsoft Defender Security Center.” This shall redirect you to the Microsoft 365 Defender for the Endpoint portal (Security & Compliance (microsoft.com)
- Under the Devices tab, select the Onboard Devices option. Please note, for this, you need to scroll a bit towards down and then towards right. And we have not done the actual onboarding yet. Have patience and wait for my fourth blog! We are going to do the Onboarding in there. There are different options to onboard. I shall be showing the way to onboard devices using Intune.
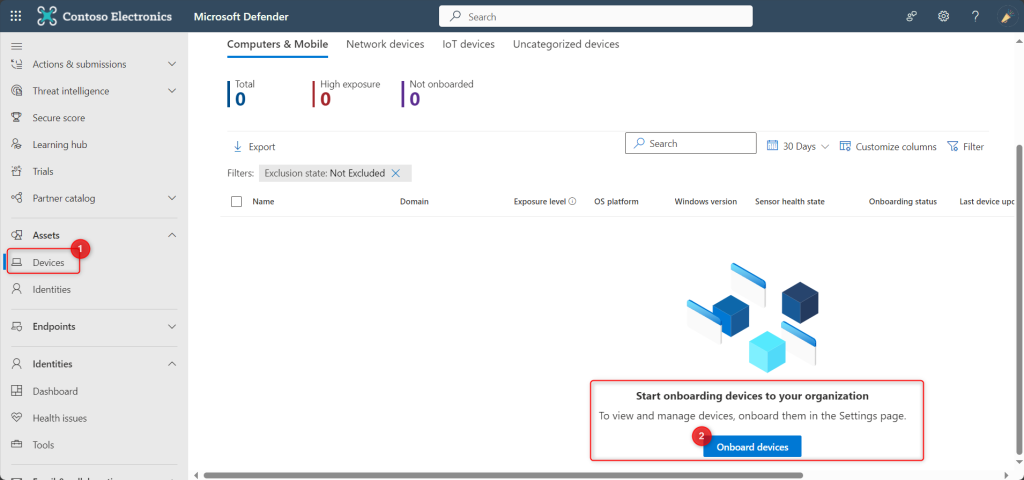
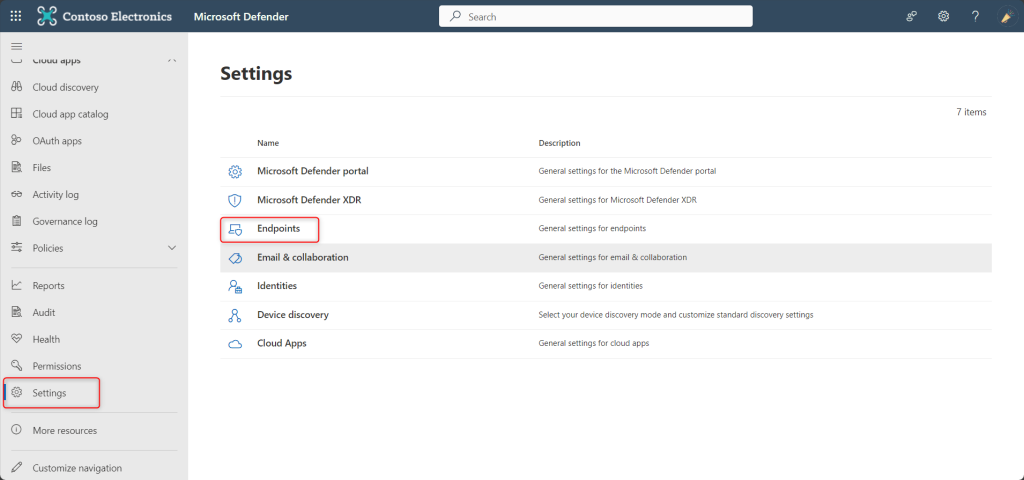
- Now click on Settings > Endpoints. An important point to be noted is, you shall not see the option for ‘Endpoints’ unless you perform the 4th Step above (Onboard devices)
- Now click on Advanced Features and scroll down. You will see the the toggle switch for the Microsoft Intune connection . Set this setting to On.
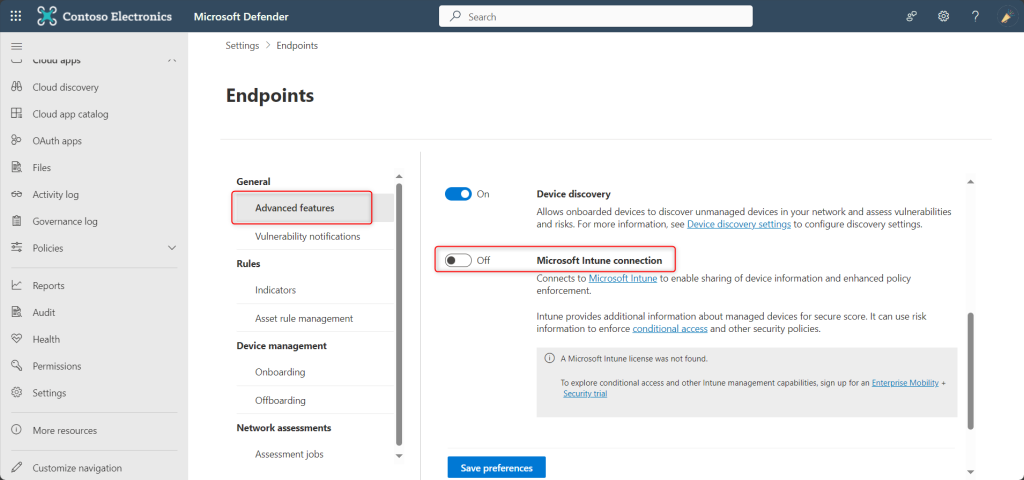
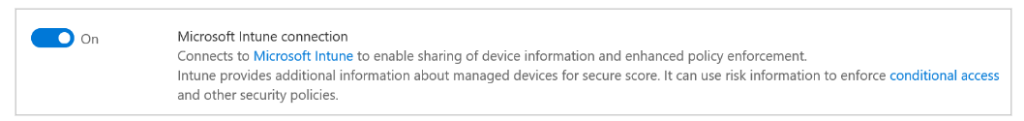
Enable Microsoft Defender for Endpoint in Intune
💡 Please Note: If the Connection status at the top of the page is already set to Enabled, the connection to Intune has already been made. In such case, you can select Open the Microsoft Defender for Endpoint admin console to open the Microsoft Defender Security Center. Then use the guidance in the following steps to confirm that the Microsoft Intune connection is set to On.
- Select Save preferences. Now go back to the Intune portal. The connection status is still Unavailable.

- Click on Refresh. After refreshing, the Connection status is Available and shows the Last synchronized date as below.

💡 Please Note: Once the connection between Microsoft Defender for Endpoint and Microsoft Intune is established, the services are expected to sync with each other at least once every 24 hours. The number of days without sync until the connection is considered unresponsive can be configured in the Microsoft Endpoint Manager admin center.
Select Endpoint security > Microsoft Defender for Endpoint > Number of days until partner is unresponsive. - Certainly by now, the Microsoft Defender for Endpoint is enabled with Microsoft Intune.From the Intune admin center, you can easily Enable the Endpoint Security Profile settings .You can easily Enable or Disable some of the settings from the above window.
- Furthermore, now you need to configure Microsoft Defender for Endpoint to use compliance and app protection policies. For this, go to Microsoft Defender for Endpoint page in the Microsoft Endpoint Manager admin center.
- Configure the following under MDM Compliance Policy Settings for Windows10/11, iOS or Androids:
- Set Connect Android devices to Microsoft Defender for Endpoint to On.
- Set Connect iOS devices to Microsoft Defender for Endpoint to On.
- Set Connect Windows devices to Microsoft Defender for Endpoint to On. Now, the following devices are connected to Microsoft Defender for Endpoint for compliance:
- Applicable devices that you manage with Intune.
- Devices you enroll in the future.
12. To use Microsoft Defender for Endpoint with MAM, configure the App Protection Policy Settings for Android and iOS only:
-
- Set Connect Android devices to Microsoft Defender for Endpoint for app protection policy evaluation to On.
- Set Connect iOS devices to Microsoft Defender for Endpoint for app protection policy evaluation to On.
13. Select Save.

💡 Please Note: When you integrate a new application to Intune Mobile Threat Defense and enable the connection to Intune, Intune creates a classic conditional access policy in Microsoft Entra ID (Microsoft Azure).
Nevertheless, with each MTD app is integrated, including Microsoft Defender for Endpoint or any of Microsoft’s MTD partners, a new classic conditional access policy is created. These policies can be ignored; however, they shouldn’t be edited, deleted, or disabled.If the classic policy is deleted, you must delete the connection to Intune that was responsible for its creation. Once you delete the connection, you must then set it up again. Doing so recreates the classic policy. Migrating classic policies for MTD apps to the new policy type for conditional access isn’t supported.
Classic conditional access policies for MTD apps:
- Are used by Intune MTD to require that devices are registered in Microsoft Entra ID. With this, it is ensured that they have a device ID before communicating to MTD partners. The ID is required, so that devices can successfully report their status to Intune.
- Have no effect on any other Cloud apps or resources.
- Are distinct from conditional access policies you can create to help manage MTD.
- By default, don’t interact with other conditional access policies you use for evaluation.
Further to view classic conditional access policies in Azure, go to Microsoft Entra ID > Conditional Access > Classic policies.
Hence, I hope that today I have been able to give you a step-wise approach to integrate this strong tool of Microsoft Defender for Endpoint with Microsoft Intune.
Moreover, would you want to go to the other topics and revise? Well, here you goooo!
- Part 1: Microsoft Defender for Endpoint Series-Introduction
- Part 2: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint-In detail
- Part 3: Microsoft Defender for Endpoint Series- Integration of Microsoft Intune with Microsoft Defender for Endpoint
- Part 4: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint Onboarding Process using Microsoft Intune for Windows
- Part-5: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint Offboarding Process using Microsoft Intune
- Part 6: Microsoft Defender for Endpoint Series- Policy Creation to Set Device-Risk Level for Microsoft Defender for Endpoint
- Part 7: Microsoft Defender for Endpoint Series-Threat and Vulnerability Management
- Part 8: Microsoft Defender for Endpoint Series-Microsoft Defender for Endpoint Capabilities
- Part 9: Microsoft Defender for Endpoint Series-Microsoft Threat and Vulnearbility Management Capabilities
- Part 10: Microsoft Defender for Endpoint Series-Microsoft Defender for Endpoint Testground
- Connect Microsoft Defender for Endpoint to Intune
Also, strongly believe that – ‘The fastest way to learn and retain a skill is, to teach it!‘ . Lastly, we recommend to stay tuned with us to progress on Microsoft Defender for Endpoint Chronicles. This is just the beginning.🌟
Author: Salona Sahni Kapoor aka Intunesiastic
cubic solutions GmbH
