Policy Creation to Set Device-Risk Level for Microsoft Defender for Endpoint
Do you often find forums discussing Microsoft Defender for Endpoint and its features, but still have questions in mind?
🚀A one-stop solution for all your questions- We have started a Microsoft Defender for Endpoint Series, where we want to cover topics on a deeper level and discover the possibilities with all kinds of threats and endpoints!
- Learn Microsoft Defender for Endpoint with #Salona aka #Intunesiastic
As seen in my earlier blogs from the Microsoft Defender for Endpoint Series, Microsoft Defender for Endpoint Series-Part 3 and Microsoft Defender for Endpoint Series-Part 4, we have already learnt to integrate Microsoft Intune and Microsoft Defender for Endpoint. We also learnt about onboarding & offboarding of a Windows device to Microsoft Defender for Endpoint using Microsoft Intune.
Let me tell you, we are not yet completely finished with what all we need for Microsoft Defender for Endpoint to function! Let us take the next step. But before that, I would like to sincerely thank my MEM Community for joining me, Salona aka #Intunesiastic in this journey of Microsoft Defender for Endpoint Series.
Today we shall get to know about the different kinds of Policies and their sole purpose in terms of Defender for Endpoint. Ofcourse this post shall also explain the steps in detail for these policy creations.
Compliance Policy creation to set Device-Risk Level for Windows
The compliance policy determines the level of risk that an organization considers as acceptable for its devices. The following information is specific to configuring Microsoft Defender for Endpoint as part of a compliance policy:
- Sign in to the Microsoft Intune admin center.
- Select Devices > Compliance policies > Policies > Create Policy.
- Select the Platform field, and then select Windows 10 and later in the drop-down menu
- Select Create to open the Create policy configuration window.
- Enter a Name that helps you identify this policy later. You can optionally enter a Description.
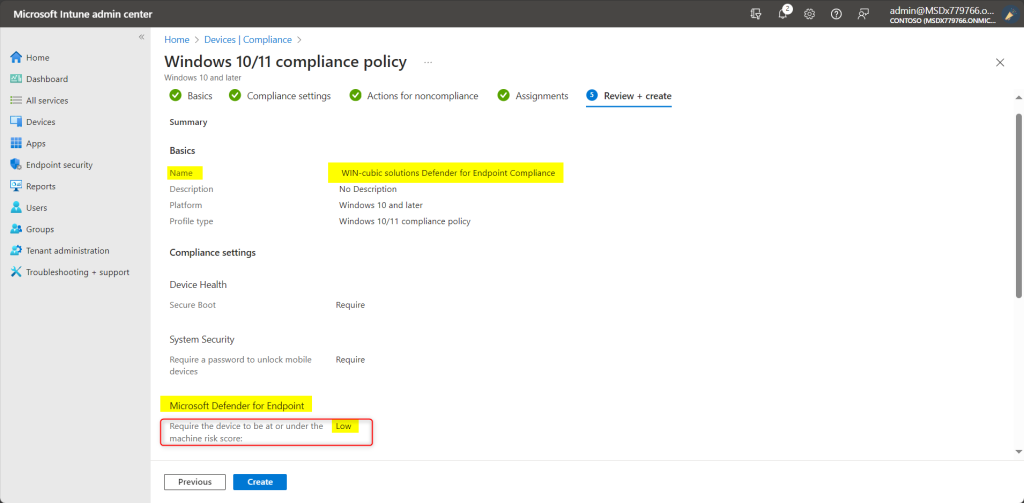
- On the Compliance settings tab, expand the Microsoft Defender for Endpoint group. Then set the option titled “Require the device to be at or under the machine risk score” to your preferred level. Threat level classifications are determined by Microsoft Defender for Endpoint.
- Clear. This level is the most secure. The device can’t have any existing threats and still access company resources. If any threats are found, the device is evaluated as noncompliant. (Microsoft Defender for Endpoint uses the value Secure.)
- Low. The device is compliant if only low-level threats exist. Devices with medium or high threat levels aren’t compliant.
- Medium. The device is compliant if the threats found on the device are low or medium. If high-level threats are detected, the device is determined as noncompliant.
- High. This level is the least secure and allows all threat levels. Devices with high, medium, or low threat levels are considered compliant.
- Complete the configuration of the policy, including assignment of the policy to applicable groups.
For more information, please refer to :
- Create a compliance policy in Microsoft Intune.
- Windows compliance settings in Microsoft Intune | Microsoft Learn
The snapshot below shows a sample compliance policy access creation:
App Protection (MAM) Policy creation to set Device-Risk Level for Windows
The following information is specific to configuring Microsoft Defender for Endpoint as part of the application protection policy:
- Sign in to the Microsoft Intune admin center.
- Select Apps > App protection policies. This selection opens the App protection policies details.
- Select Create policy and select Windows 10 and later. Enter a policy Name and an optional Description.
- Click Next to display the Apps page. Choose which apps should be targeted by this policy. You must add at least one app. (eg: Microsoft Edge)
- Click Next to display the Data protection page. You can control the movement of data into and out of the context of org protection. The org context is defined by documents, services, and sites accessed by the specified org account. The following policy settings help control external data received into the org context and org data sent out of the org context.
- Receive data from
- Send org data to
- Allow cut, copy, and paste for
- Printing Org data
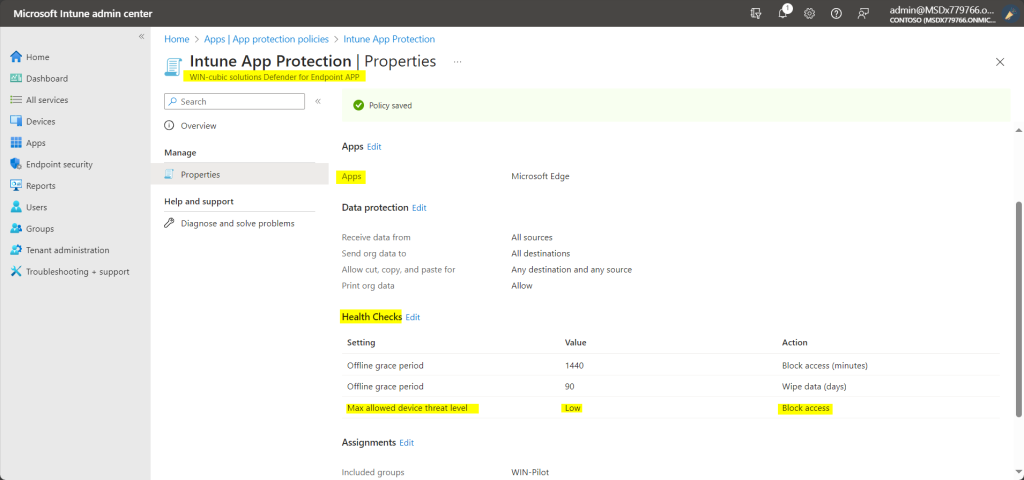
- Click Next to display the Health Checks page. Select the below options:
- App conditions
- Device conditions . It is important here to select the Max allowed device threat level with the Device Actions as (Block Access/Wipe Data)
- Complete the configuration of the policy, including assignment of the policy to applicable groups.
The snapshot below shows a sample application protection policy creation:
Conditional Access Policy creation to Grant/Block Access for Windows
Conditional access policies can block access to resources for devices that exceed the threat level set by their organization. Access from the device can be blocked to corporate resources, such as SharePoint Online or Exchange Online. The policies can use data from Microsoft Defender for Endpoint to determine which devices should be blocked.
- Sign in to the Microsoft Intune admin center.
- Select Endpoint security > Conditional Access > New policy.
- Enter a policy Name and an optional Description.
- Select Users and groups. Use the Include or Exclude options to add your groups to the policy, and then select Done.
- Select Cloud apps, and then select which apps to protect. For example, choose Select apps and then select Office 365 SharePoint Online and Office 365 Exchange Online. Select Done to save your changes.
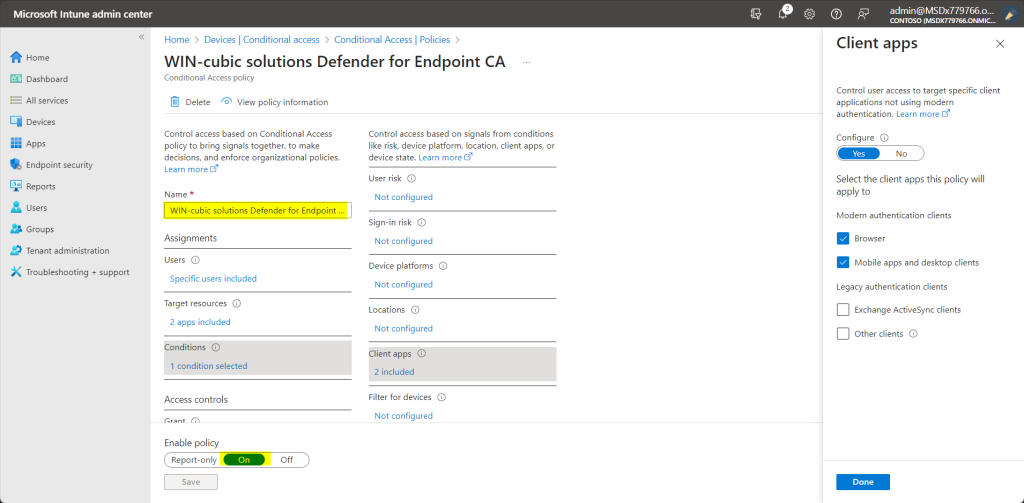
- Select Conditions > Client apps to apply the policy to apps and browsers. For example, select Yes, and then enable Browser and Mobile apps and desktop clients. Select Done to save your changes.
- Select Grant to apply Conditional Access based on device compliance. For example, select Grant access > Require device to be marked as compliant. Choose Select to save your changes.
- Select Enable policy, and then select Create to save your changes.
The snapshot below shows a sample conditional access policy creation:
Hence, I hope that today I have been able to give you a step-wise approach regarding the kinds of Policies needed in terms of Defender for Endpoint. Moreover, would you want to go to the other topics and revise? Well, here you goooo!
- Part 1: Microsoft Defender for Endpoint Series-Introduction
- Part 2: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint-In detail
- Part 3: Microsoft Defender for Endpoint Series- Integration of Microsoft Intune with Microsoft Defender for Endpoint
- Part 4: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint Onboarding Process using Microsoft Intune for Windows
- Part-5: Microsoft Defender for Endpoint Series- Microsoft Defender for Endpoint Offboarding Process using Microsoft Intune
- Part 6: Microsoft Defender for Endpoint Series- Policy Creation to Set Device-Risk Level for Microsoft Defender for Endpoint
- Part 7: Microsoft Defender for Endpoint Series-Threat and Vulnerability Management
- Part 8: Microsoft Defender for Endpoint Series-Microsoft Defender for Endpoint Capabilities
- Part 9: Microsoft Defender for Endpoint Series-Microsoft Threat and Vulnearbility Management Capabilities
- Part 10: Microsoft Defender for Endpoint Series-Microsoft Defender for Endpoint Testground
Also, I strongly believe that – ‘The fastest way to learn and retain a skill is, to teach it!‘
Lastly, we recommend to stay tuned with us to progress on Microsoft Defender for Endpoint Chronicles. This is just the beginning.🌟
Author: Salona Sahni Kapoor aka Intunesiastic
cubic solutions GmbH
